As an AWS customer you inherit all the best practices of AWS Security Services like policies, architecture, and operational processes. The AWS Cloud enables a shared responsibility model. AWS manages security OF the cloud, you are responsible for security IN the cloud. You retain control of the security you choose to implement to protect your own content, platform, applications, systems, and networks no differently than you would in an on-site data center.
Benefits of AWS Security
- Keep Your Data Safe – the AWS infrastructure puts strong safeguards in place to help.
- Protect your privacy – All data is stored in highly secure AWS data centers.
- Meet Compliance Requirements – AWS manages dozens of compliance programs in its infrastructure. This means that segments of your compliance have already been completed.
- Save Money – cut costs by using AWS data centers. Maintain the highest standard of s security without having to manage your own facility.
- Scale Quickly – security scales with your AWS Cloud usage. No matter the size of your business, the AWS infrastructure is designed to keep your data safe.
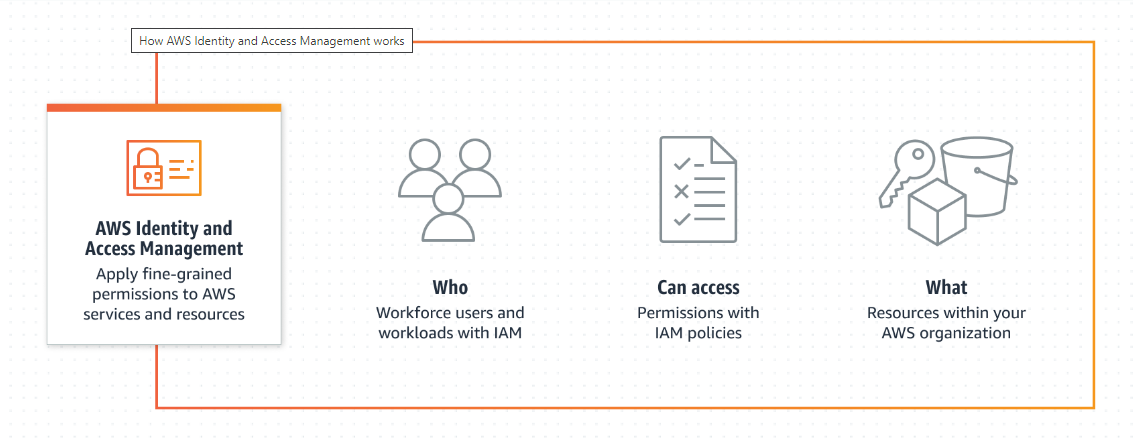
AWS Identitiy and Access Management(IAM)
- Set and manage guardrails and fine-grained access controls for your workforce and workloads.
- Manage identities across single AWS accounts or centrally connect identities to multiple AWS accounts.
- Grant temporary security credentials for workloads that access your AWS resources.
- Continually analyze access to right-size permissions on the journey to least privilege.
Compliance
AWS Cloud Compliance enables you to understand the robust controls in place at AWS to maintain security and data protection in the cloud. As systems are built on top of AWS Cloud infrastructure, compliance responsibilities will be shared. Compliance programs include: Certifications / attestations. Laws, regulations, and privacy. Alignments / frameworks.
AWS Artifact
AWS Artifact is your go-to, central resource for compliance-related information that matters to you. It provides on-demand access to AWS’ security and compliance reports and select online agreements. Reports available in AWS Artifact include our Service Organization Control (SOC) reports, Payment Card Industry (PCI) reports, and certifications from accreditation bodies across geographies and compliance verticals that validate the implementation and operating effectiveness of AWS security controls. Agreements available in AWS Artifact include the Business Associate Addendum (BAA) and the Nondisclosure Agreement (NDA).
Amazon GuardDuty
Amazon GuardDuty offers threat detection and continuous security monitoring for malicious or unauthorized behavior to help you protect your AWS accounts and workloads. Intelligent threat detection service. Detects account compromise, instance compromise, malicious reconnaissance, and bucket compromise.
Continuous monitoring for events across: AWS CloudTrail Management Events. AWS CloudTrail S3 Data Events. Amazon VPC Flow Logs. DNS Logs.
AWS WAF & AWS Shield WAF
AWS WAF is a web application firewall. Protects against common exploits that could compromise application availability, compromise security or consume excessive resources. WAF lets you create rules to filter web traffic based on conditions that include IP addresses, HTTP headers and body, or custom URIs. WAF makes it easy to create rules that block common web exploits like SQL injection and cross site scripting. The rules are known as Web ACLs.
Shield: AWS Shield is a managed Distributed Denial of Service (DDoS) protection service. Safeguards web application running on AWS with always-on detection and automatic inline mitigations. Helps to minimize application downtime and latency. Two tiers – Standard and Advanced.
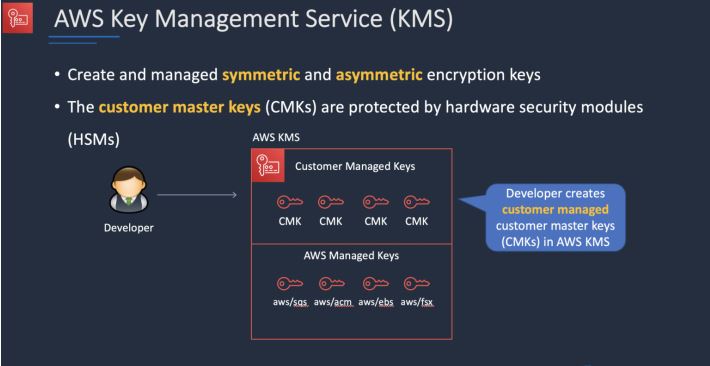
AWS Key Management Service
AWS Key Management Service gives you centralized control over the encryption keys used to protect your data. You can create, import, rotate, disable, delete, define usage policies for, and audit the use of encryption keys used to encrypt your data.
AWS KMS is integrated with AWS CloudTrail which provides you the ability to audit who used which keys, on which resources, and when. AWS KMS enables developers to easily encrypt data, whether through 1- click encryption in the AWS Management Console, or using the AWS SDK to easily add encryption in their application code.
AWS CloudHSM
AWS CloudHSM is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud. With CloudHSM, you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. CloudHSM offers you the flexibility to integrate with your applications using industry-standard APIs, such as PKCS#11, Java Cryptography Extensions (JCE), and Microsoft CryptoNG (CNG) libraries.
AWS Inspector:
Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS. Inspector automatically assesses applications for vulnerabilities or deviations from best practices. Uses an agent installed on EC2 instances. Instances must be tagged.
AWS Trusted Advisor:
Trusted Advisor is an online resource that helps to reduce cost, increase performance and improve security by optimizing your AWS environment. Trusted Advisor provides real time guidance to help you provision your resources following best practices. Advisor will advise you on Cost Optimization, Performance, Security, and Fault Tolerance.
Trusted Advisor scans your AWS infrastructure and compares is to AWS best practices in five categories:
- Cost Optimization.
- Security.
- Fault Tolerance.
- Service Limits.
- Trusted Advisor comes in two versions. Core Checks and Recommendations (free)
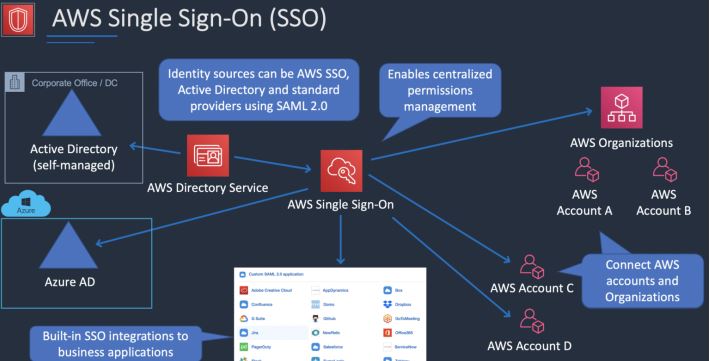
AWS Single Sign-On (AWS SSO)
AWS Single Sign-On is a cloud-based single sign-on (SSO) service that makes it easy to centrally manage SSO access to all of your AWS accounts and cloud applications.
It helps you manage SSO access and user permissions across all your AWS accounts in AWS Organizations.
AWS SSO also helps you manage access and permissions to commonly used third-party software as a service (SaaS) applications, AWS SSO[1]integrated applications as well as custom applications that support Security Assertion Markup Language (SAML) 2.0.
AWS SSO includes a user portal where your end-users can find and access all their assigned AWS accounts, cloud applications, and custom applications in one place.
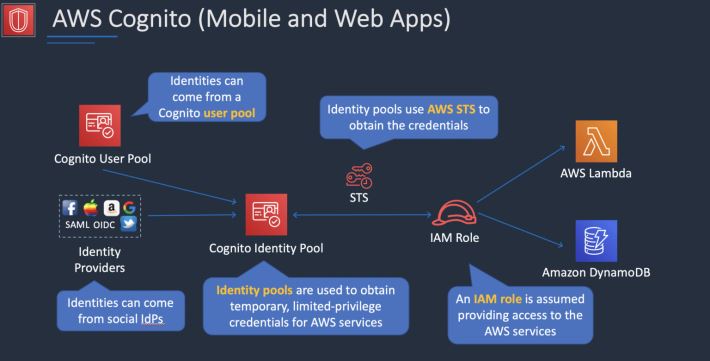
Amazon Cognito
Amazon Cognito lets you add user sign-up, sign-in, and access control to your web and mobile apps quickly and easily.
Amazon Cognito scales to millions of users and supports sign-in with social identity providers, such as Apple, Facebook, Google, and Amazon, and enterprise identity providers via SAML 2.0 and OpenID Connect.
The two main components of AWS Cognito are user pools and identity pools:
- User pools are user directories that provide sign-up and sign-in options for your app users.
- Identity pools enable you to grant your users access to other AWS services.
You can use identity pools and user pools separately or together.
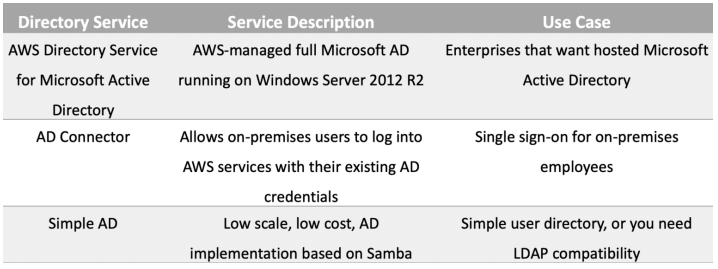
AWS Directory Services
AWS provide a number of directory types. The following three types currently feature on the exam and will be covered on this page:
Active Directory Service for Microsoft Active Directory.
- Simple AD.
- AD Connector.
As an alternative to the AWS Directory service you can build your own Microsoft AD DCs in the AWS cloud (on EC2). The table below summarises the directory services covered on this page as well as a couple of others, and provides some typical use cases: